
Scriptly Helps Pharmacies Identify Trends in Real Time with Reveal

The Reveal embedded business intelligence platform is based on a cloud architecture that includes multiple authentication methods, local caching of data to minimize sending of queries to servers and databases, and much more. We’ll explore these in this blog. Authentication Reveal Cloud authentication uses the OpenID Connect (OIDC) standard. The Identity Service component provides secure authentication […]
The Reveal embedded business intelligence platform is based on a cloud architecture that includes multiple authentication methods, local caching of data to minimize sending of queries to servers and databases, and much more. We’ll explore these in this blog.
Reveal Cloud authentication uses the OpenID Connect (OIDC) standard. The Identity Service component provides secure authentication against multiple authentication sources, including Google, Office 365 and Infragistics accounts.
Reveal follows the standard flow for OIDC authentication, as you can see in the below diagram that highlights authentication using Microsoft.
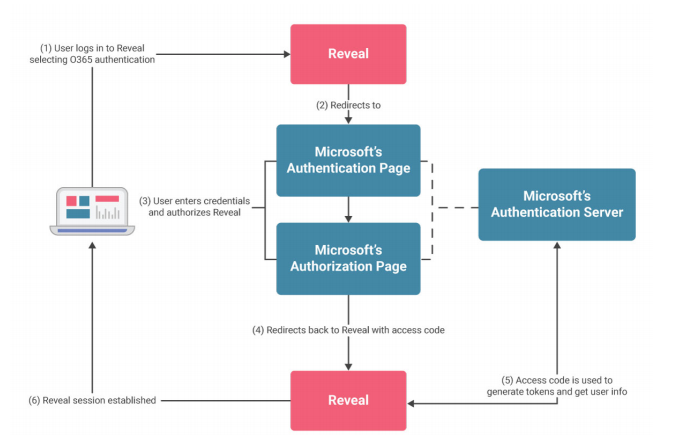
Note that Reveal never has access to the user’s credentials as they are entered in a page provided by the authentication provider (Google, Microsoft or Infragistics). The authentication provider then redirects the user to Reveal with an access code (step 4). Reveal then uses this code to get user information, such as the email address that identifies the user, and tokens that will be used to access other services, including Google Drive for Google accounts or SharePoint and OneDrive for Microsoft O365 accounts.
Reveal supports multiple data sources such as:
To authenticate any of these data sources is dependent on the provider and each typically requires a different authentication method. Reveal supports four types of authentication:
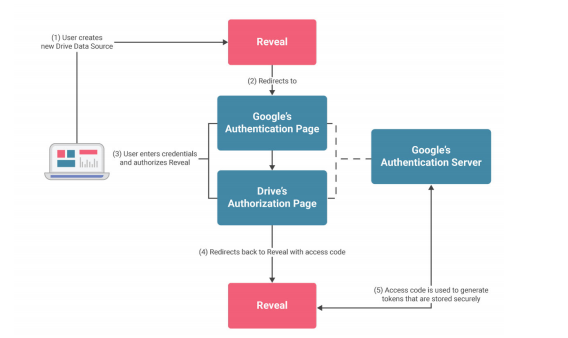
For those providers supporting OAuth such as Google Drive, Dropbox, OneDrive and others Reveal will redirect users to the authentication page provided by the data provider requesting permission to access its data. You can see this below:
“>
The process is similar to that with OIDC we discussed earlier. Once authentication is complete, Reveal will store the authentication tokens in order to access the data on behalf of the user across all supported platforms.
To improve performance, Reveal stores cached data locally in the device, thereby minimizing the number of queries sent to the server or database. Credentials to access data sources are also stored in the device as they are requested only when the data source is configured or used for the first time.